Stored XSS on TP-Link WR740N
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NThis is an easy machine from TryHackMe.
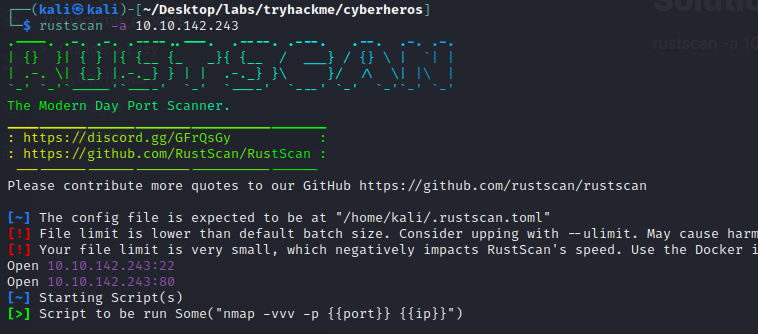
Running some scans reveals the ports 22 (SSH) and 80 (HTTP).
rustscan -a 10.10.142.243
After observing the source code, we see that the authentication mechanism is on the client side (which is a very insecure piece of code, since we can leverage the Javascript to get a cleartext username and password):
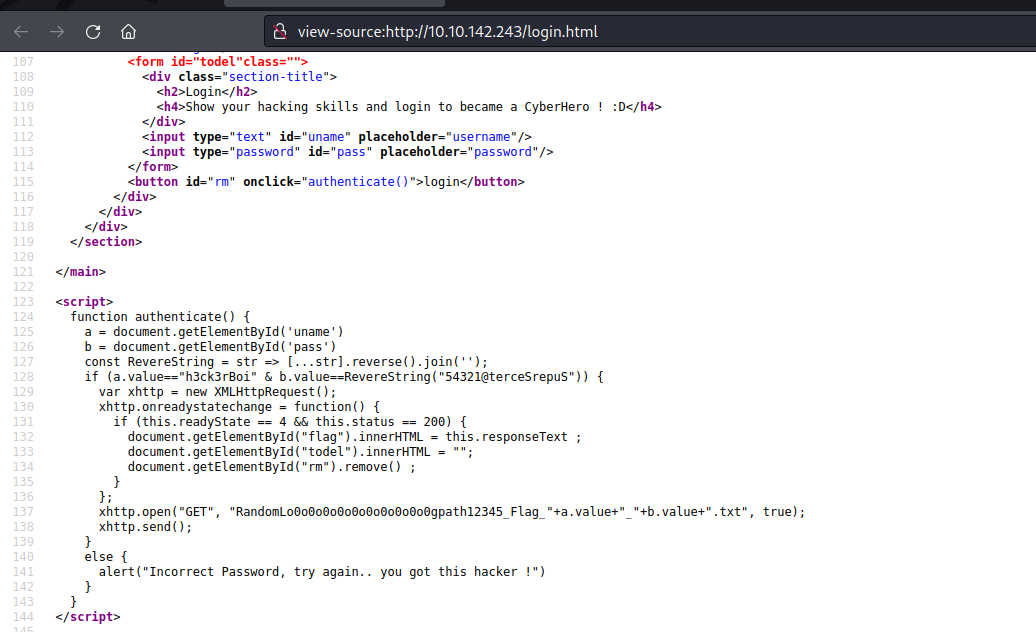
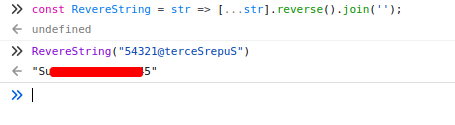
So we first receive the arguments for the user and password via "getElementById" functions. The comparison against the user is fairly simple, we just have to check if the user submitted is equals to "h3ck3rBoi". For the password, we also need to insert something that equals to the result of "ReverseString(54321@terceSrepuS')". It is pretty straightforward to get the result just by consulting the Javascript documentation. If you are lazy like me, you can use the Javascript console to get the correct password by declaring the function in the console and use that same function to evaluate the result of the string "54321@terceSrepuS":
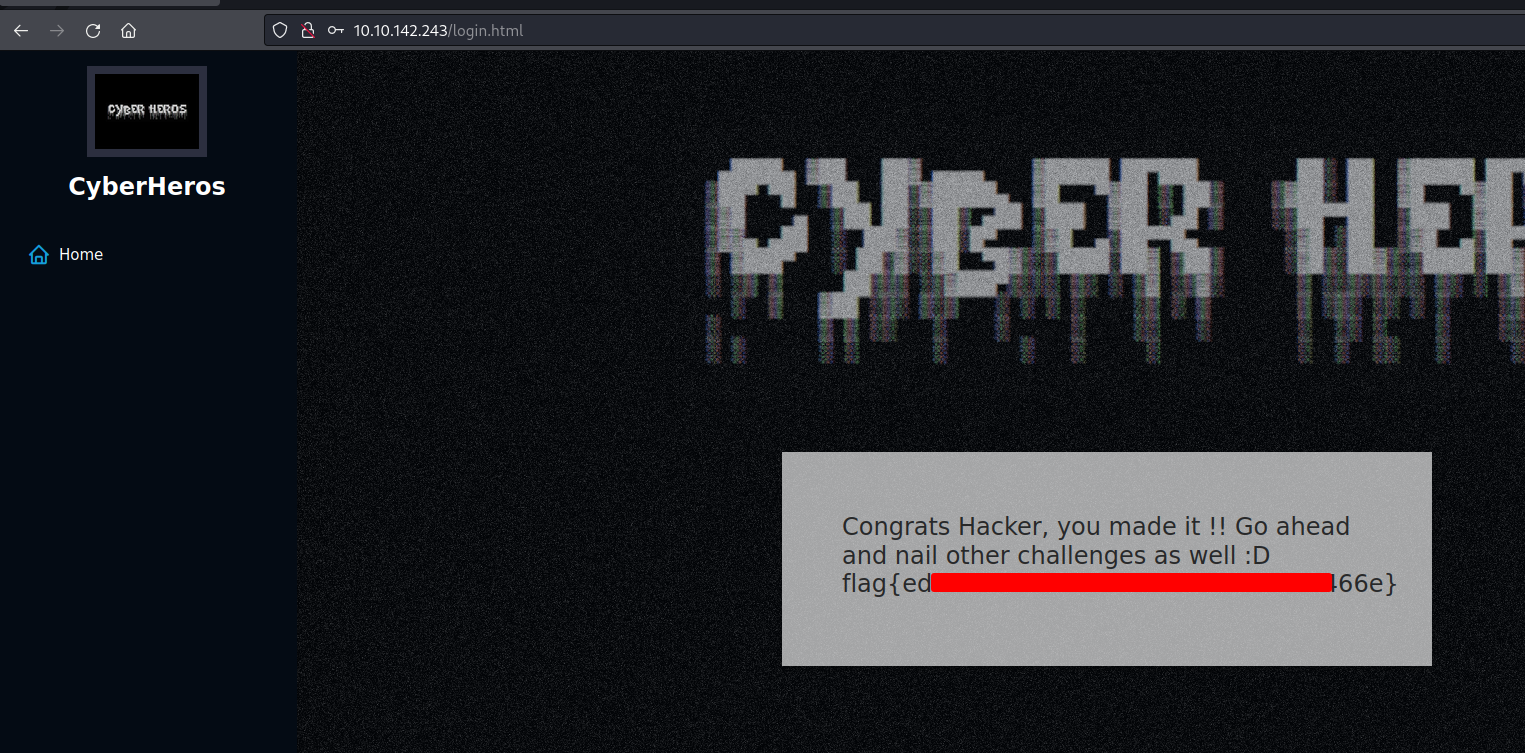
Now that we know the the username and the password, we can login onto the application and retrieve the flag:
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NTP-Link WR740N suffers from an LFI vulnerability in the /help/ directory.
research tp-link-WR740NThis is an “easy” machine from HackTheBox Business CTF.
writeup hackthebox ctfThis is an easy machine from TryHackMe.
writeup tryhackmeThis is an easy machine from TryHackMe.
writeup tryhackme